Πανελλήνιες - Αρχαία Ελληνικά: Καταργείται η μετάφραση στο γνωστό - Λιγότερα μόρια από το άγνωστο | Alfavita

Almásy Csilla Gerinckoncepció - TUDTAD? ... hogy miért is hatékony, funkcionális és gerincbarát egyben az úgynevezett „dead bug” gyakorlat a hasizmok erősítésére? Ahogy korábbi posztomban leírtam, a hasizmok valódi funkciója nem a

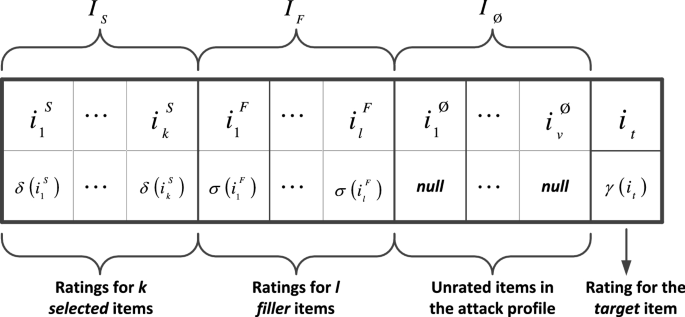
Detection of shilling attack in recommender system for YouTube video statistics using machine learning techniques | SpringerLink

Detection of shilling attack in recommender system for YouTube video statistics using machine learning techniques | SpringerLink